Further Information Regarding Westpac WIBS (Qvalent) SSH Host Key Change
Change Preparation
Preparing WinSCP with the new Known Host Key Value
Westpac urges customers which use WinSCP to consult the vendor documentation at https://winscp.net/eng/docs/ to choose a pre-change solution which best suits their environment.
Preparing OpenSSH SFTP with the new Known Host Key Value
Perform this action on your OpenSSH SFTP Client Linux/Unix server which performs the SFTP process to add the new known host key value into the list of host keys.
Note this information is general advise and may be different for your particular deployment of OpenSSH SFTP.
Copy the newly provided known host key value to your server and perform the following
cp ~/.ssh/known_hosts ~/.ssh/known_hosts.bak cat NEW_HOSTKEY_FILE >> ~/.ssh/known_hosts
To validate:
cat known_hosts
You should see two known host key values for the WIBS SFTP server environment (existing and new)
Post change day, it is highly recommended that the existing known host key value (the entry higher up in the file) be removed.
Other SFTP Client Software Pre-Change Preparation Steps
If other SFTP client software is used, please consult your vendor supplier documentation on how to add a secondary known host key into your known hosts trust store.
Westpac is unable to provide support for third-party software (ie. software not written by Westpac)
Common Issues
WinSCP
If the change preparation has not been successfully applied, a SFTP connection to the WIBS SFTP server will not be successful without manual administrative user intervention.
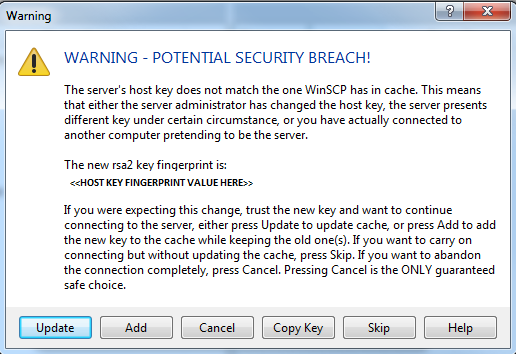
If the change is not successful, it is possible the following will be logged when running winscp.com from the command line
Searching for host... Connecting to host... Authenticating... WARNING - POTENTIAL SECURITY BREACH! The server's host key does not match the one WinSCP has in cache. This means that either the server administrator has changed the host key, the server presents different key under certain circumstance, or you have actually connected to another computer pretending to be the server. The new rsa2 key fingerprint is: ssh-rsa 2048 xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx If you were expecting this change, trust the new key and want to continue connecting to the server, either press Update to update cache, or press Add to add the new key to the cache while keeping the old one(s). If you want to carry on connecting but without updating the cache, press Skip. If you want to abandon the connection completely, press Cancel. Pressing Cancel is the ONLY guaranteed safe choice. In scripting, you should use a -hostkey switch to configure the expected host key. (U)pdate, (A)dd, Ca(n)cel (0 s), (C)opy Key, (S)kip:
And the following similar warning message will be logged on a connection attempt using the WinSCP GUI application
If this error occurs you should perform the following
- Confirm that the presented key fingerprint from the server you are connecting to matches the key value in this documentation
- If the key matches, you are communicating with the WIBS SFTP server, and you should press the ‘Update’ button to update the cached known host entry in WinSCP
- If the connection is now successful, future connections under this user on this server should now work without manual intervention
- If the presented key fingerprint from the server does not match the expected value do not proceed any further. This indicates your client is connecting directly to a non-WIBS SFTP server.
OpenSSH SFTP
If the change preparation has not been successfully applied, a SFTP connection to the WIBS SFTP server will not be successful without manual administrative user intervention.
If the change is not successful, it is possible the following will be logged when running sftp manually from the command line as the user which is running the SFTP client scripts.
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@ @ WARNING: REMOTE HOST IDENTIFICATION HAS CHANGED! @ @@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@ IT IS POSSIBLE THAT SOMEONE IS DOING SOMETHING NASTY! Someone could be eavesdropping on you right now (man-in-the-middle attack)! It is also possible that a host key has just been changed. The fingerprint for the RSA key sent by the remote host is SHA256:xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx. Please contact your system administrator. Add correct host key in /home/user/.ssh/known_hosts to get rid of this message. Offending RSA key in /home/user/.ssh/known_hosts:xx RSA host key for <SERVER> has changed and you have requested strict checking. Host key verification failed.
If this error occurs you should perform the following:
- Confirm that the presented key fingerprint from the server you are connecting to matches the values provided in this documentation
- If the key matches, you are communicating with the WIBS SFTP server, however the known host key value has not been added to the known_hosts file
- Use the process mentioned in the pre-work documentation to verify the new entry is in the known hosts file mentioned in the error output location.
- If the new entry is not in the file, use the process above to add the known host key entry into the known_hosts file
- Reattempt a connection and confirm the error is resolved. If resolved, future connections under this user on this server should now work without manual intervention
- If the presented key fingerprint from the server does not match the expected value do not proceed any further. This indicates your client is connecting directly to a non-WIBS SFTP server.
- If the key matches, you are communicating with the WIBS SFTP server, however the known host key value has not been added to the known_hosts file
Frequently Asked Questions
Do I need to send through a new Connectivity Change Request?
If your Test and Production environments are currently in an operational state pre-change, there is no requirement to send through a Connectivity Change Request in iLink
Do I need to change my SSH keypair used for authentication for this change?
This change does not affect your SSH keypair which you use for authentication and there is no requirement for them to change as a part of this change.
Do I need to change my PGP keypair used for file encryption for this change?
This change only affects SFTP.
This change does not affect your PGP keypair which you use for file encryption and there is no requirement for them to change as a part of this change.
Qvalent pushes files to our SFTP server. Do I need to change the public key used for authentication by Qvalent
This change does not affect the SSH keypair which Qvalent uses to authenticate to your SFTP server. No change is required on your SFTP server.
This change does however affect your SFTP client software for affect any files that you send to the Qvalent SFTP server hosts mentioned in the change notification using your SFTP client.
I use SFTP Client Software software which is not mentioned in the SFTP Installation Guide. What do I do to prepare for this change?
Westpac is unable to provide specific guidance for third-party client software not mentioned in our installation guide.
Please consult your SFTP client vendor documentation for more information
How do I evaluate whether my SFTP client software supports RSA 2048-bit host Keys?
2048-bit RSA has wide ranging support in most SFTP client software.
If your software does not support RSA 2048-bit keys, Westpac advises customers to investigate whether an updated version of their SFTP software is available to prepare for this change or to move to another SFTP software package which is up to date with the latest security protocols.
Westpac urges customers to perform UAT testing post-change in Support to evaluate the impact of this change on your systems and to consult SFTP client software vendor documentation
What if my SFTP connection breaks?
Customers will have two options to restore service:
1. Investigate whether you can add the known host key to the keystore by performing a manual connection (see our WinSCP and OpenSSH examples)
2. Use iLink as a BCP option for the delivery of your files between your financial systems and Westpac
This will be communicated by our helpdesk to customers who are having issues with their connectivity. Our helpdesk will be on-hand to assist customers who have issues instigating iLink BCP as a priority.
Westpac will be unable to roll this change back due to the expected impact of this change.
Can I be granted an extension for this change?
No, extensions cannot be granted for this change. Due to the nature of the key change, all customers must be prepared for this change simultaneously for this change to occur.
If you are not ready for this change, you may need to prepare to change your SFTP client software or prepare to instigate iLink BCP and how it will need to interact with your financial systems.
Will there be a way to continue using the old known host key?
No, the old host keys will be decommissioned by Westpac. There will be no way to continue using the old known host key.
How will I know my SFTP client software will work with the new host keys?
Customers are urged to use the provided Test/Support environment to evaluate the change Westpac is planning to make and your change process. Note the test environment will be upgraded on a specific date as noted in the change notification.
Also, please note as specified in this document that the known host key Westpac will be using for Production will be different to Test.
Westpac urges customers to make note of this process in Test and perform similar pre-change preparation actions in Production for the Production known host key.
My WIBS solution does not involve credit card data and therefore is not subject to PCI-DSS. Does this change still apply to me?
Yes, this change will apply to all WIBS customers that connect to the Westpac (Qvalent) SFTP servers.
What are the current, pre-change known host key values for Test and Production?
The existing known host keys for the test and production environments are as follows.
Note: These below values are NOT the new host key values. Please refer to the change advise for the new values you need to prepare your system for.
Host | ssiw.qvalent.com (Production WIBS SFTP Server – Current Pre-Change Known Host Key Value |
| MD5 Fingerprint | f3:32:2b:56:64:a1:0d:63:32:f6:a2:4f:66:f3:ca:e3 |
| Bubble-Babble Fingerprint | xuhon-zepum-sokag-soros-docyv-bisih-helip-demyl-tafiz-livat-myxix |
| SHA-256 Fingerprint | nlhLHW+iJMYb0IM4/5GRDJHTHX5P7Wv1WFZYOxt+iDA |
| SSH Known Host Key | ssiw.qvalent.com,192.170.86.151 ssh-dss AAAAB3NzaC1kc3MAAACBAIVqXUaUz3jxc1g5MoMV+ZotN6FNjx8Lmi/lu7ogxgUWIo3l6ifG3pREXTwxD8zlZeBHO6szRv3plN3naXngWXzzmQKPheSOGYi4cM1R0Ls3b4XolhbhAJ3ho4FGNKKx0liUzYiO6dYlLQ0aj9pJQgdqr4iKKyOOgXoaDW6Pw9pTAAAAFQC81S5lcRiiUwFjzBkcnDI3/9BTrwAAAIBfHCQrdUuWIAFiewZaI5ECaEj3Q9aJ8YPDvSt4YW7dNJ+stVg4Vipnqbc+T6gQ/DKZrx1MAeU9p9KtF/anc6+rSbveBdORUlPqFLvAFvh8A9/rmSFuEvuvCWCNjzw2N9yzMoI//HrJmPXgUJUwrMQkLDQfIzstoNmJYqxNkV73QAAAIBNVV3W4m7QfffdNdp7dfYFDD0JzmrHOW2A84QEwtRXeJoZCbg4mNryne1KOQYVmW1u3y3Xbp0bfpt53T5+a4wcYOyb8J5f9FgSHbpE45HOJdpUio3aR0IpAZBQMYabNqz65HdB4xz1TDb2hY78ndoyM3tPwZe6C3z5VHcFS0DXLA== |
| Host | ssiw.support.qvalent.com (Test/Support WIBS SFTP Server - Current Pre-Change Known Host Key Value |
| MD5 Fingerprint | 1e:95:71:61:c7:36:42:cd:82:d5:f3:94:fa:ca:35:df |
| Bubble-Babble Fingerprint | xunep-gyhim-nocos-visav-gybec-dofyh-tisyk-dered-nekos-dakoz-roxex |
| SHA-256 Fingerprint | 3wOJEECDVxbWV+PJ0ZmoNTz1oKT/JLT5oDgoQha+mCQ |
| SSH Known Host Key | ssiw.support.qvalent.com,203.39.159.31 ssh-dss AAAAB3NzaC1kc3MAAACBAJUn0moaQk8uEFfCcsuyKxhrZbbR4/CUAPfscIC5vQSHtAAv6IS+JMuvOqJJO8SPKOCCuwXdCOvCHc5YITC5EcFPJruEp9R6gOcGcDFQQSUT21lks2ohD6fKTH+I+WNZj9cipORqKm232I9280+hi+S+NukROe6xic6cCHnN/y+dAAAAFQCEtz08KQ4CdE6LjLi85X9Xv+OaeQAAAIBkqqVcBv3G0ExtHKxP8jpYfKx9Wm+JZGxKyrFt5smvZA3wuPaU4H4sv3G/AxqiOpgvGeIKpk2F2+Y6KUAF6ewXxLqBLrvEWzZ60A/QFDwhdSWyNv8gBtA3MyTPfQv6TTJb2aZlw7EvyyWMiOL0qdzYOC1f8T9vTg4VgTzT9NqA8QAAAIEAjx12nTMFlMfzGGgCKyYVCj19yaFtvl3b7YrDAtvjVbpk+8Uc+JRIppOb5tCSwDxyC3WWdCdJyAHtr4g7dlASakYszqs1gpgybkDtH3H6+BcjKMaoZLKNQ6f+YJtzt5Y87879jRpQsCCqsyhkm8gbuLXf1Rp6gQkoKf+My1RpO+A= |
Note: The above values are NOT the new host key values. Please refer to the change advise for the new values you need to prepare your system for.